Digital Hijacking: When Hackers Attack Airlines Instead of Airplanes
Explore how elite cybercrime groups, including Scattered Spider, are digitally hijacking airlines—disrupting booking systems, flight ops, and passenger data—without ever touching a plane. Learn what’s at stake, real-world incidents, and how the aviation industry must respond.

WASHINGTON D.C., July 1, 2025
The idea of airline hijacking has changed a lot. It’s no longer about masked figures taking over cockpits; it’s about hackers disrupting lives online. Today’s cybercriminals, especially the Scattered Spider group, are focusing on airlines’ IT systems. They target booking platforms, crew management, and passenger databases. They can shut down operations and put personal data at risk, all without ever boarding a plane. This blog examines this troubling trend, looking at the tactics of these actors, real-world cases, and how the aviation industry can respond to navigate this new era of digital hijacking.
The New Threat Landscape: Digital Hijacking Defined
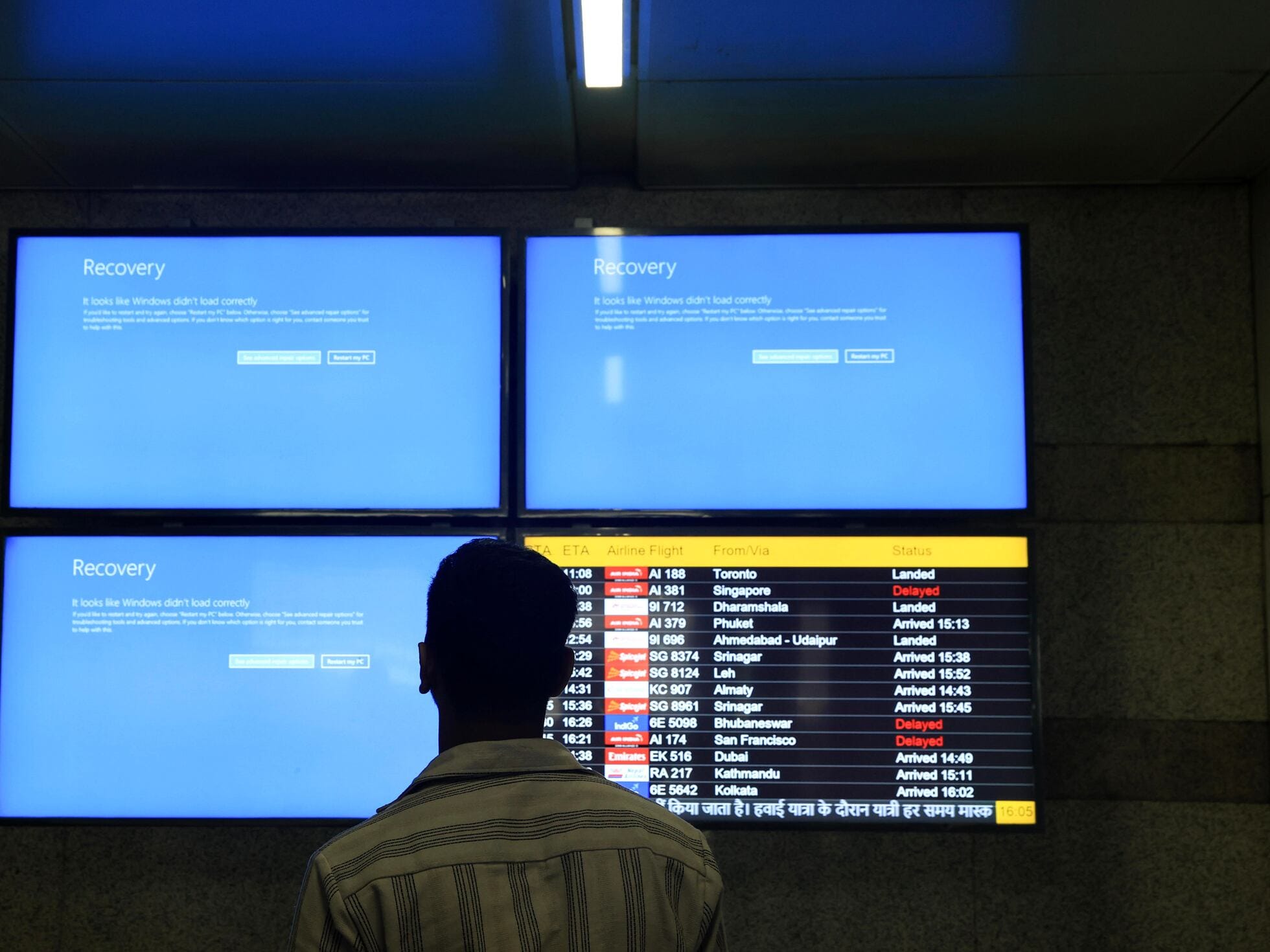
Airlines have digitized nearly every part of their operations: e-ticketing, mobile apps, operations dashboards, crew scheduling, baggage tracking, and more. While this brings convenience, it also exposes them to cyber threats. Recent attacks by groups like Killnet and state-backed actors showed how DDoS attacks on airport websites can confuse the public. More advanced threats, such as those from ransomware groups, are now getting into airline backend systems, causing shutdowns and ransom demands.
Global IT outages, like the July 2024 CrowdStrike and Microsoft glitch that affected over 1,300 flights and caused tens of thousands of delays across Europe and the U.S., highlight how fragile the aviation sector has become. Unlike accidental outages, today’s digital hijacks have malicious intent, and the stakes are significantly higher.

Meet Scattered Spider—From Casinos to Cockpits
Scattered Spider, also known as UNC3944 or Muddled Libra, is linked to major ransomware incidents that hit MGM Resorts and Caesars in 2023. This group has become a serious cyber threat.
What makes them particularly dangerous?
- Social engineering skills: They impersonate IT help desk staff, take advantage of MFA fatigue, and use SIM-swaps to breach security.
- Stealthy tactics: Once inside, they use legitimate tools (like Mimikatz, Fleetdeck.io, Screenconnect, Pulseway) to avoid detection.
- Data theft and ransomware: They steal data and may encrypt backups—a tactic used against Hiltons and Caesars.
In late June 2025, both Google’s Mandiant and Palo Alto Networks reported that Scattered Spider has turned its attention to the aviation and transportation sectors.
Charles Carmakal from Mandiant said that “These primary characteristic intrusions we’ve observed in the airline industry align precisely with the complex, social-engineering-led patterns of Scattered Spider.”
Case Studies: Airlines on the Digital Attackbed
Hawaiian Airlines – June 26, 2025
Hawaiian Airlines reported a cybersecurity incident that affected “some of our IT systems.” Flights continued as normal, but the airline described the situation in terms usually associated with ransomware attacks. The FAA confirmed that flight safety remained intact, but investigations are still underway. Security researchers now believe Hawaiian Airlines is a likely first victim of Scattered Spider’s aviation targeting.
WestJet – June 13, 2025
WestJet in Canada had an internal systems breach, causing problems with their booking app. Law enforcement, including the RCMP and FBI, got involved. Flights operated normally, but passenger data and internal systems were compromised.

Stakes Are High: Data, Disruptions, and Public Trust
These digital hijacks may not lead to physical harm, but their effects are significant:
- Passenger data and regulatory risk: Airlines keep sensitive information such as passport numbers, payment info, and travel history. A breach could result in GDPR or PIPEDA penalties.
- Costly operational delays: Even small IT disruptions can snowball in tightly scheduled networks, costing millions each day.
- Reputational damage: Trust can fade quickly. News about data loss or extortion can push customers to competitors and damage airline brands.
- Regulatory scrutiny: Agencies like the FAA and CISA are demanding better cybersecurity standards for aviation systems following incidents.
These attacks highlight the harsh reality: airline IT systems are now part of critical infrastructure and must be treated accordingly.
Anatomy of a Digital Hijacking
Here’s how Scattered Spider-style breaches happen:
- Reconnaissance: Criminals gather intel through LinkedIn, social media, and data-breach dumps.
- Phishing or help desk attacks: Spoofed emails or calls trick employees into clicking harmful links or installing remote tools.
- MFA bypass/fatigue: Attackers repeatedly ask for MFA codes, wearing down victims until they gain access.
- Privilege escalation and lateral movement: Using stolen credentials and tools like Mimikatz, they navigate corporate networks to target key systems.
- Data theft and ransomware: They exfiltrate sensitive data and encrypt backups or operational systems, demanding payment.
The strategy is simple: exploit human trust first, then quietly break into systems before launching high-stakes attacks.
Industry Response: Hardening the Defenses
CISA and FBI guidelines for airlines and critical infrastructure recommend:
- Prepare for social engineering: Strengthen help desk procedures and train staff to verify identities and recognize MFA fatigue.
- Deploy phishing-resistant MFA: Implement FIDO2/WebAuthn or PKI-based authentication to block common bypass methods.
- Limit remote access tools: Review and monitor RMM tools; only allow approved software and restrict access.
- Conduct incident simulations: Use MITRE ATT&CK techniques to test defenses in realistic attack scenarios.
- Maintain offline backups: Regularly back up all data, ensuring it is offline and secure against ransomware.
What Happens Next?
Airlines need to act quickly to build cyber resilience:
- Start tabletop drills now: Simulate a Scattered Spider-style breach involving operations, legal, PR, and technical teams.
- Adopt a Zero Trust model: Assume internal networks aren’t secure; enforce least privilege and strict network separation.
- Centralize threat intelligence: Work with IATA, TSA, and FBI threat-sharing platforms to stay ahead of new tactics.
- Invest in endpoint detection: Use EDR solutions that can identify living-off-the-land methods and suspicious lateral movement.
- Commit to staff training: Regularly test for vulnerabilities in social engineering and reinforce verification protocols.
Simply fixing vulnerabilities won’t be enough—airlines must rethink their entire defense approach around people, processes, and technology.
The Final Descent: Where the Airline Industry Lands on Cyber Risk
Digital hijackings are not mere possibilities; they are immediate threats reshaping cybersecurity in aviation. Reacting after a breach is too late; proactive and smart cyber defenses are necessary for safety.
Securing the Skies, Digitally: What Should Happen Next?
In a world where hijackers no longer take over cockpits but hack into servers, how should airlines redesign their security strategies concerning staff training, vendor management, technology investment, and industry collaboration to stay ahead of digital hijackers?
Sources
Cyberattack Incidents & Industry Response:
- Reuters (June 26, 2025) – Hawaiian Airlines cyberattack: Link
- Axios (June 27, 2025) – Scattered Spider targeting airlines: Link
- FBI–CISA Alert (AA23-320A) – Threat actor tactics: Link
Expert Commentary & Quotes:
- Charles Carmakal (CISA, Mandiant) – via public statements and Axios
Visuals & Media Sources:
- Cyber Security News (LinkedIn infographic – Scattered Spider alert)
- El País (Global tech outage image, July 2024)
- ABC News (LAX screen disruption, 2022)
- Custom visuals from Shutterstock/press imagery for hackers at work




